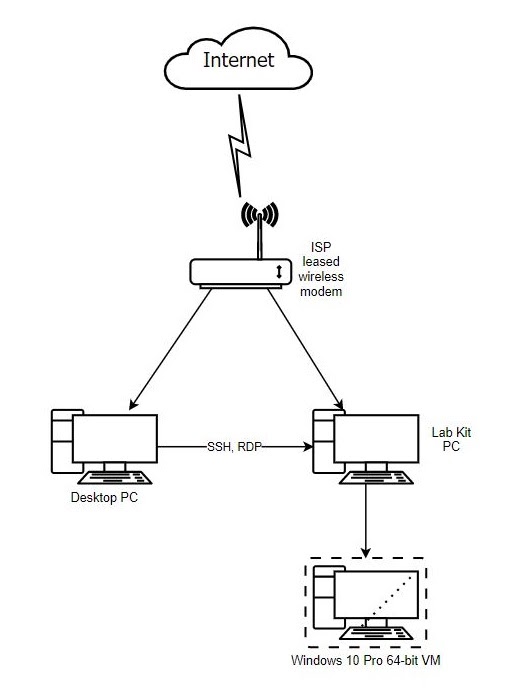
In computer operations jargon, we have clients and servers. Servers are dedicated host systems whose sole purpose is to run a specific software or service (like hosting a web site). In this configuration, the personal Windows 10 computer will act as the client and only access the server as needed. The benefit of this configuration is that if we ever need to reformat the personal Win 10 system, we can do so without affecting the home lab. Here's the desired outcome:
Command Line
Low-level computer commands such as rebooting and shutting down are best issued via command line in Linux, in case other applications and services have crashed. From the Ubuntu Linux desktop, you can access the command line by selecting your apps menu and opening Terminal Emulator.
The Ubuntu box can be rebooted with a sudo reboot now.
SSH
Secure Shell (SSH) lets us remotely access the command line of our Ubuntu box. The industry once upon a time used Telnet for this purpose, but SSH via port 22 is more modern and supports password authentication and encrypted session traffic. To establish SSH access, install an OpenSSH server on the Ubuntu box. Ubuntu usually comes prepackaged with an SSH client, but you'll need the OpenSSH server package in order to host SSH protocol and connect from an external system.
OpenSSH server can be installed with the apt-get package manager tool. First, update the package manager itself. The package updater will verbosely describe the actions it is taking, then finish with something like the following:
Once packages are up to date, you're ready to install SSH Server.
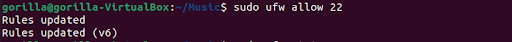
Once it's installed, don't forget to create a Linux firewall rule with the command sudo ufw allow 22, assuming you're running the firewall service (which you probably should as best practice/for experience).
You can test connectivity by opening a shell from your PC to the Ubuntu box. To do so, open any terminal program (like Command Prompt, Powershell, or Git Bash) and type ssh [user]@[ipaddress] to initialize an SSH session. It should prompt you for a password.
XRDP
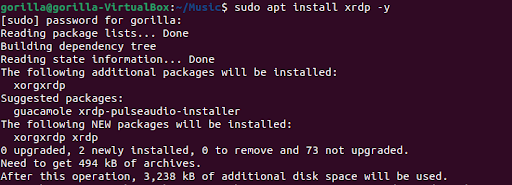
On Windows 10, the de facto software to access another computer's desktop is the Remote Desktop Protocol (RDP) on port 3389. It's by no means a high-security solution, but the low latency and simplicity of use are much appreciated on a local computer-to-computer connection. The catch in our case is that we're not connecting to another Windows PC; we're connecting to Ubuntu Linux, so we'll need to load some software to help Ubuntu use the RDP protocol. XRDP to the rescue! XRDP will allow you to use RDP from a Windows 10 PC to establish persistent remote desktop access to the virtualization server. To use XRDP, you'll need to install it on the Ubuntu box first. Here are the commands:
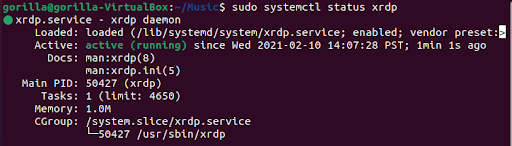
Verify that the XRDP service is up and running.
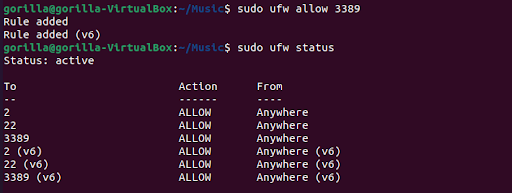
To wrap up the XRDP installation, run a sudo ufw to allow 3389 to open up port 3389 for RDP usage. Alternatively, for better security practice, you might want to restrict which IPs can access the Ubuntu box's 3389 port using sudo ufw allow from [IP] to any port 3389 instead of the general open port configuration.
Once you've got the port opened, test and confirm RDP access from your personal system.
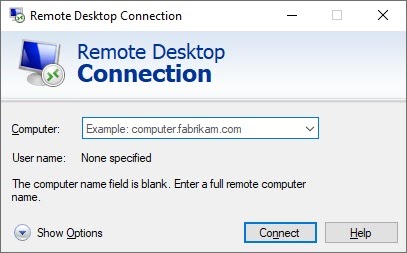
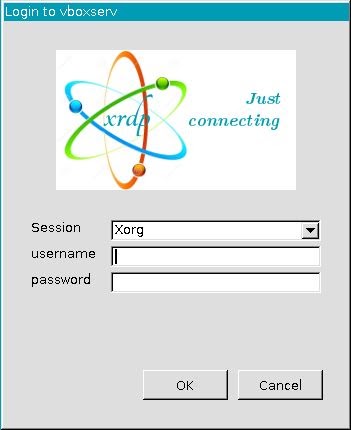
By using this method, you won't enter credentials until you reach the login screen below. This differs significantly from how Windows-to-Windows RDP works, but once you see it in action, you'll quickly acclimate to the process!
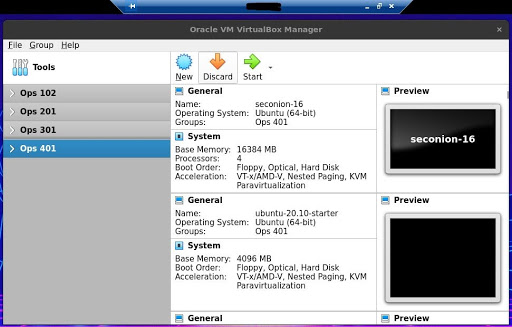
The final outcome is a RDP window with the signature blue ribbon at the top. Here's a screencap of me running VirtualBox on the remote Ubuntu PC.
WinSCP
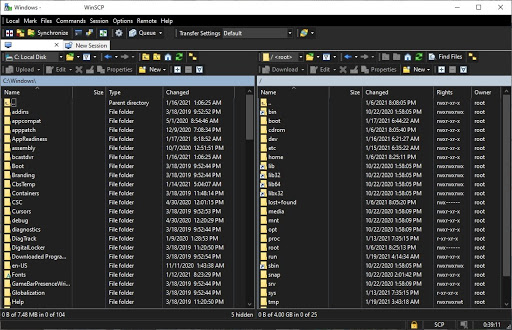
The last consideration for administering a home cyber range remotely is how to transfer files to and fro efficiently over the home network. The easiest solution for this in lieu of a home file server is using WinSCP to facilitate the drag-and-drop file transfer. WinSCP authenticates using your Ubuntu credentials via port 22 and can save your credentials in a convenient fashion.
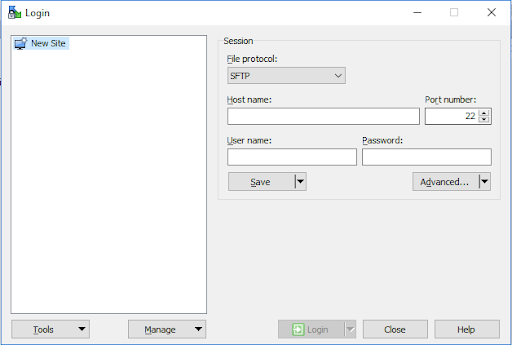
After you've established connectivity to the Ubuntu PC, you can perform simple graphical drag-and-drop operations between the systems for efficient file transfer. This is a great convenience factor between host systems, but should not be deployed to our virtual machines themselves once we start working with malware.
Conclusion
Our home cyber range is starting to come together. Now that we have three ways to communicate with the Ubuntu system (SSH, RDP, and SCP), we can store the hardware in a more convenient location and free up desk space for our personal system only. If this process intrigues you, join us for our Code Fellows Ops 102 virtual workshop, where we perform this home lab setup together as a group.
In my next article, I'll dive into how Security Onion can be deployed to VirtualBox as our primary VM for threat detection activities. Until then, happy “labbing”!

